How Can We Detect SSH Attacks on Linux Servers?

Servers with open SSH ports are commonly exposed to continuous brute-force attacks by bots. These bots typically start by scanning ports and then proceed to attempt password guessing through brute-force methods on open ports, such as the SSH port, in an effort to infiltrate the server.
Since these attacks are carried out by bots, they can persist for months or even years without stopping. The attacking bots will continue their attempts until they reach their target. Due to the fact that these attacks come from hundreds of different IP addresses and locations, IP banning is not a viable solution.
How to Detect SSH Attacks?
To determine if our server is under an SSH attack, we can examine the daily logs of our Linux server. In Linux servers, logs related to login activities are kept within the "auth.log" file as shown below:
/var/log/auth.log
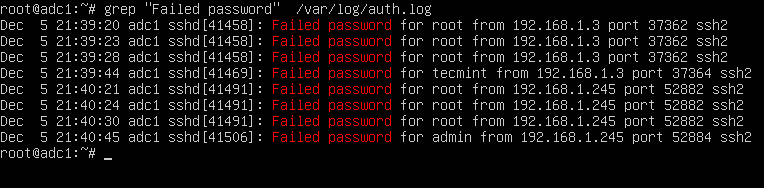
Within this file, we can identify unsuccessful login attempts on our server by searching for "Failed password." To do this, we can execute the following command:
grep "Failed password" /var/log/auth.log
For CentOS/RHEL-based servers, the following command can be used:
egrep "Failed|Failure" /var/log/secure
How Can I Protect My Server from SSH Attacks?
- Close the SSH port to external access
- Establish connections using a static IP
- Connect through a proxy server
- Use MFA for user authentication
The most secure way is to close the SSH port to external access. With Protect Remote, you can close your SSH port to external access without the need for static IP usage, allowing connections only from authorized devices.
Office
Harju maakond, Tallinn, Kesklinna linnaosa, Ahtri tn 12, 15551 Estonia
Contact Us